Use Microsoft Entra ID groups claims
You can transfer group assignments from Microsoft Entra ID to a Neptune DXP - Open Edition system.
| This procedure describes configuration aspects of the Neptune DXP - Open Edition authentication settings. As these directly affect the system security, these configuration steps must be thoroughly tested in an appropriate test environment. |
Prerequisites
-
You have created an enterprise application / app registration in Microsoft Entra ID.
-
You have configured an authentication method of type “Microsoft Entra ID” on the Neptune DXP - Open Edition system using this app registration.
-
You have defined the identically named security groups in the Neptune DXP - Open Edition system that you expect in the token claims.
Procedure
-
Sign in to the Microsoft Entra admin center.
-
To define the desired groups in Microsoft Entra ID, select Manage → Groups.
-
To assign users to groups as required, select Groups → <Your group> → Manage → Members.
-
Sign in to the Microsoft Azure Portal.
-
To assign a group to an enterprise application, select Enterprise Applications → <Your Application> → Manage → Users and Groups → Add User/Group.

-
To maintain the token claim groups configuration on the app registration, select App registrations → <Your Application> → Manage → Token Configuration → Add groups claim.
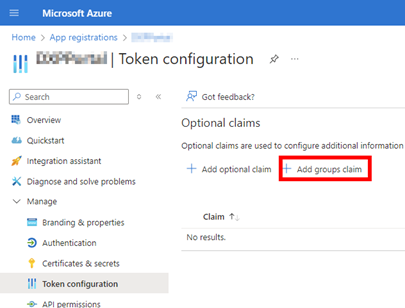
-
In the Edit groups claim details screen, select Groups assigned to the application (recommended for large enterprise companies to avoid exceeding the limit on the number of groups a token can emit).
-
Select sAMAccountName for all token types.
-
Select Add.
-
To ensure a correct transfer of the group names, you need to edit the app registration manifest. Select App registrations → <Your Application> → Manage → Manifest.
-
Edit the JSON manifest to include the property
"cloud_displayname"in the ID token.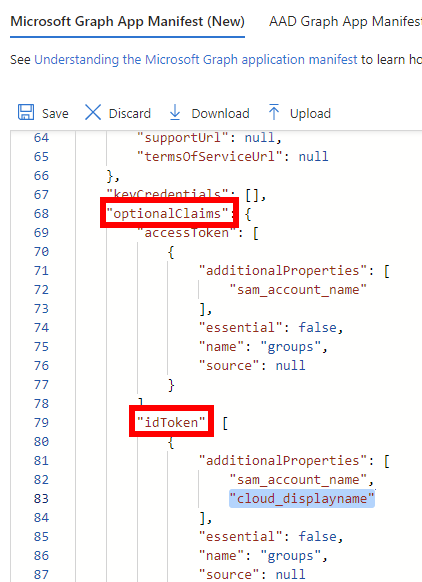
-
Save the changed manifest.