SAP Open ID Connect (SOIDC)
Introduction
The Open ID Connect authentication flow is easiest and most modern authentication mechanism to be used. It also works with tokens to authenticate the user. In contrast to the SAP (SOAUTH2) authentication flow the SAP system will not take the role of managing the authentication tokens but rather trust the provided Bearer tokens on ICF Http calls. Also, this authentication method is fully implemented into the whole ICF of SAP regardless of the service type. So, any ICF node can make use of that authentication mechanism out of the box. Acting as an OpenID Relying Party (RP), the SAP System delegates user authentication to a distinct system known as the OpenID Provider (OP). SAP has also added a propretary Bearer forwarding mode, which greatly simplifies the authentication process for Neptune Mobile Clients.
The Autentication is done through the ID Token not Access Token as its bearer.
| To use this authentication mechanism out of the box, your SAP system needs the minimum release of SAP BASIS 7.56 SP1. SAP also provides SAP Notes that would allow you to downport the OpenID Connect feature sets down to 7.52 (see SAP Note 3313726). You can check if OIDC is available in your system by checking the existence of transaction SOIDC. It is recommended to update to the latest support note for OIDC that is supported by the platform. Some IdP (e.g Microsoft Entra/Azure) need support custom claim setup and this is only available from feature pack 2. It is also recommended to schedule the report specified in note 3111813 - section 3.1. This will keep the certificate information automatically up to date if anything changes on the provider. |
Settings
- OAuth Flow Provider
-
Select SAP Open ID Connect (SOIDC) to use the OIDC authentication mechanism.
- OAuth 2.0 Client ID
-
Name of the Client ID that you configured in SOIDC. See more information at One Time Setup.
- OpenID Configuration URL path
-
The URL to the well-known openid-configuration file. In most IdP it will be accessible through the path …/.well-known/openid-configuration. This standardized configuration file contains all information necessary for the client and SAP system to configure the OpenID connection.
Examples for well-known URLs:
-
Microsoft: https://login.microsoftonline.com/yourTenant/v2.0/.well-known/openid-configuration
-
SAP BTP IAS: https://yourIASAccount.accounts.ondemand.com/.well-known/openid-configuration
-
OKTA: https://yourOktaDomain.okta.com/.well-known/openid-configuration?client_id=yourClientID
- Overridable Defaults
-
In this section you can override configuration parameters for the OIDC flow. This is only required in special cases as all necessary configuration is embedded within the …/.well-known/openid-configuration url. The well-known OpenID configuration is automatically fetched when starting the authentication flow to ensure correct configuration values that are configured in the OpenID Provider.
- Static Token Encryption
-
By setting this flag, the access token will no longer be tied to the SAP system the Mobile Client was created on.
One Time Setup
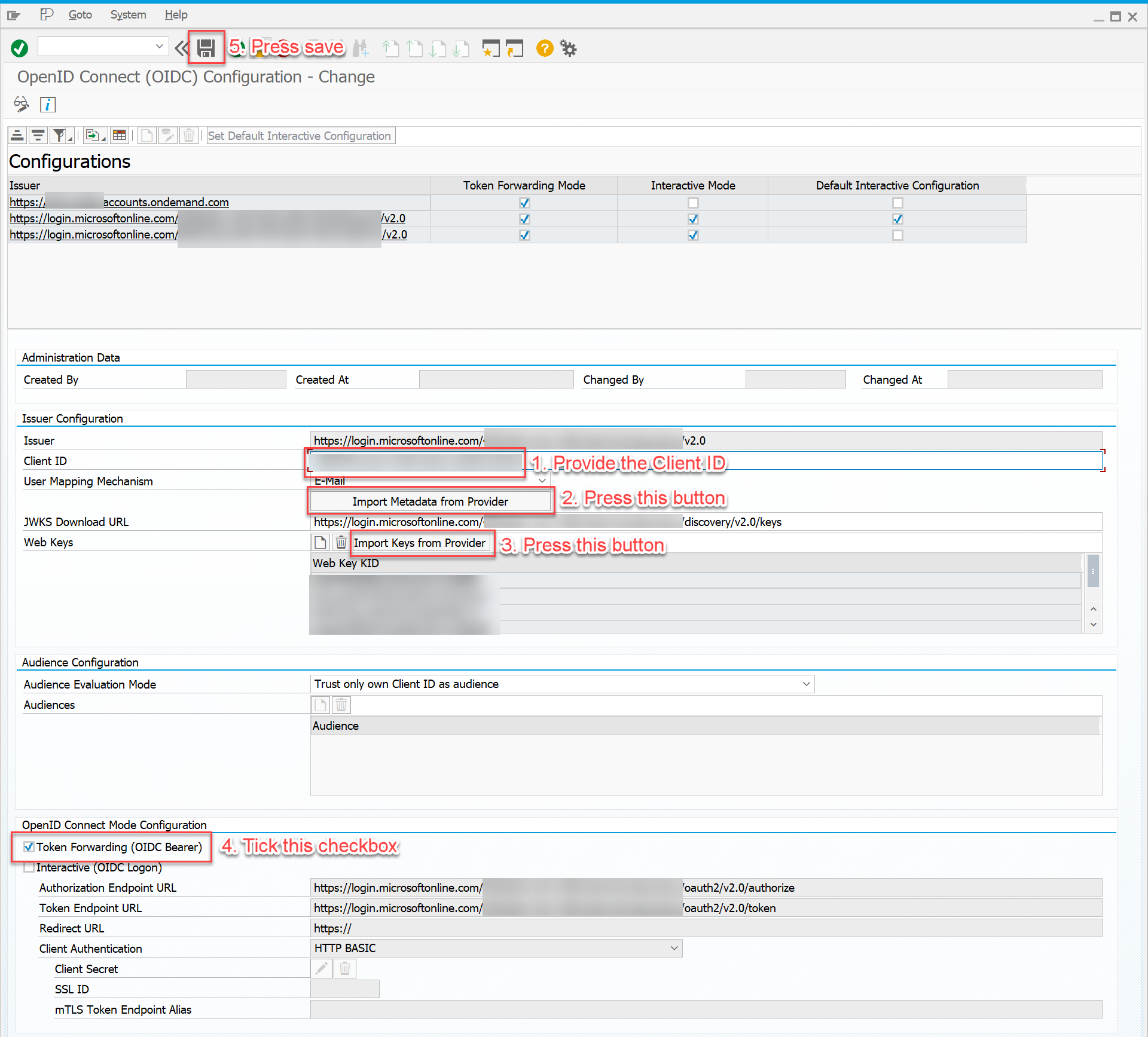
Open Transaction SOIDC and create a new issuer by clicking the button "Create" on top.
| You can find the Issuer inside the …/.well-known/openid-configuration json (property issuer). |
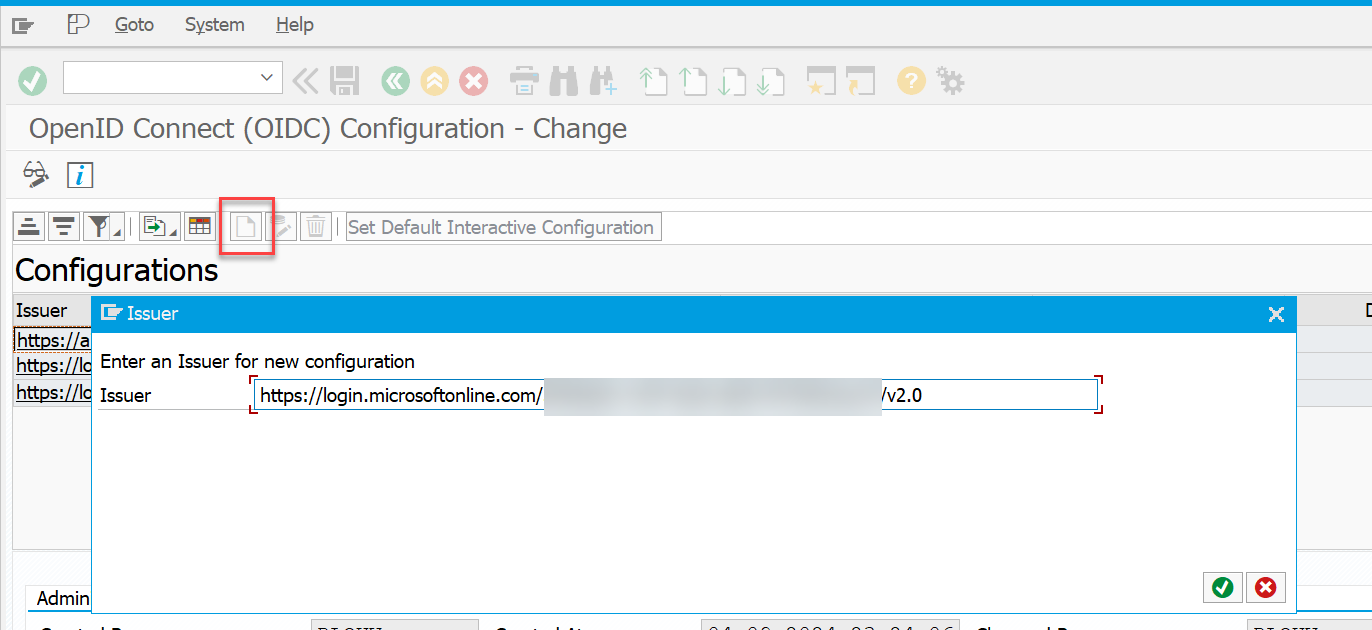 Example Issuer Urls:
Example Issuer Urls:
-
Microsoft: https://login.microsoftonline.com/yourTenant/v2.0
-
SAP BTP IAS: https://yourIAStenant.accounts.ondemand.com
-
OKTA: https://yourOktaDomain.okta.com/
Enter the Client ID of your OIDC application. You will find the Client ID (sometimes also referred to as application ID) on your OpenID provider.
Press the Button "Import Metadata from Provider".
Press the Button "Import Keys from Provider".
Tick the checkbox "Token Forward (OIDC Bearer)".
Save the configuration by pressing the Save button on top.