Configure a SAML authentication
In this topic, you learn how to set up an authentication via SAML and how to configure it in your Cockpit.
Prerequisites
-
You have registered the DXP - Open Edition in the Microsoft Entra admin center. Find more information about how to register an app in the Microsoft documentation.
-
You know the Display Name and your client ID from Microsoft Entra ID.
-
In the Microsoft Entra admin center, you have added users and groups to the DXP - Open Edition.
-
You have downloaded the SAML certificate from the Microsoft Entra admin center.
Procedure
Add a redirect URI
-
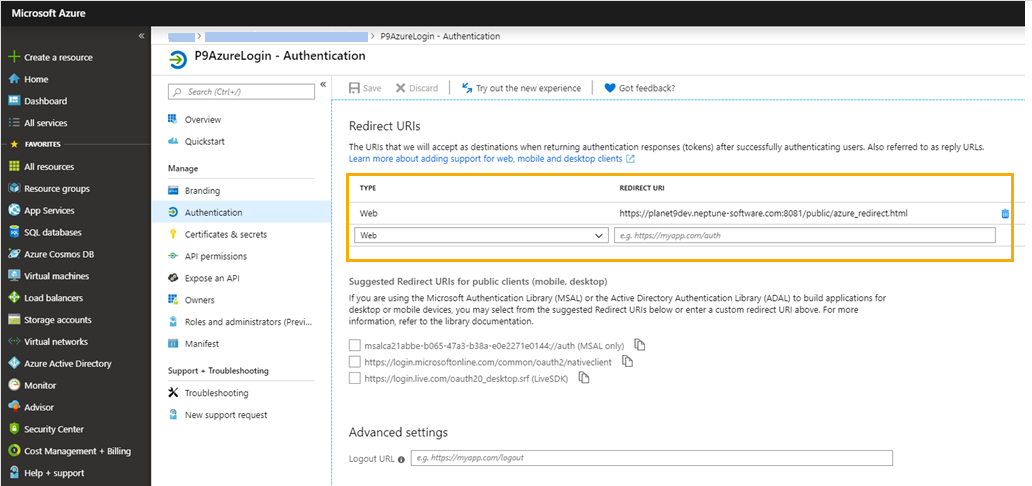
In the Microsoft Entra admin center, in Applications, select your application. Under Manage select Authentication.
-
In Redirect URI, add URIs for a web and/or a public client. These URIs will be accepted as destinations when returning authentication responses (tokens) after authenticating users.
For more information, refer to Neptune Community. The redirect URI must have the following format:
https://<Planet 9 URL>/user/logon/saml/<path>
For example:
https://planet9dev.neptune-software.com:8081/user/logon/saml/developers
Add SAML authentication provider in the Neptune DXP - Open Edition
-
In the Cockpit, go to Settings, and click System Settings.
-
Navigate to the Authentication tab and click Edit.
-
Click Add, and select SAML.
Result: The Authentication dialog opens.
-
In SAML, fill in or check the following fields:
-
Enter a Name for the authentication.
-
Check Active to activate this authentication method.
-
Check Show on login page to display the authentication method on the login page.
-
Enter a Description.
-
Enter a Login URL, use the following format:
https://myapps.microsoft.com/signin/<Display Name>/<Application(Client) ID>
Change
<Display Name>to your app display name, and change<Application (Client) ID>to your app client ID.You find Display name and Application (client) ID in Microsoft Entra ID. -
In Logout URL, enter the login URL, use the following format:
https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0
-
In Redirect URL, enter the URLs that will be accepted as destinations in a Neptune DXP - Open Edition when returning authentication responses (tokens) after successfully authenticating users and redirect users to apps mentioned in Neptune DXP - Open Edition. For example, if users should be directed to a particular launchpad, then you can add the link of that launchpad here.
-
Enter the Path to the external SAML login data.
Do not enter the path when you use the login screen. In this case, you must set the path according to the following:
http://planet9server/logon/saml/path -
In Issuer, enter the entity from the Microsoft Entra admin center that has verified the certificate content:
<Application(Client) ID>. -
Add identifier format for single sign-on (SSO).
-
In Binding, select HTTP redirect or HTTP Post.
-
In Cert (ldp), enter the certificate from the Microsoft Entra admin center.
-
Optional: In Public Key(SP), enter the public key from the Microsoft Entra Admin Center.
-
Optional: In Private Key(SP), enter the private key from the Microsoft Entra Admin Center.
-
-
-
In Claims Assignment, click Add to add claims assignments.
-
If required, in Auto Assignment, assign roles and groups that you have defined in the Role and Security Group tools in the Cockpit.
-
In Custom Script, you can enter your code (optional) to tweak the roles' assignment manually.
-
Click OK to confirm.