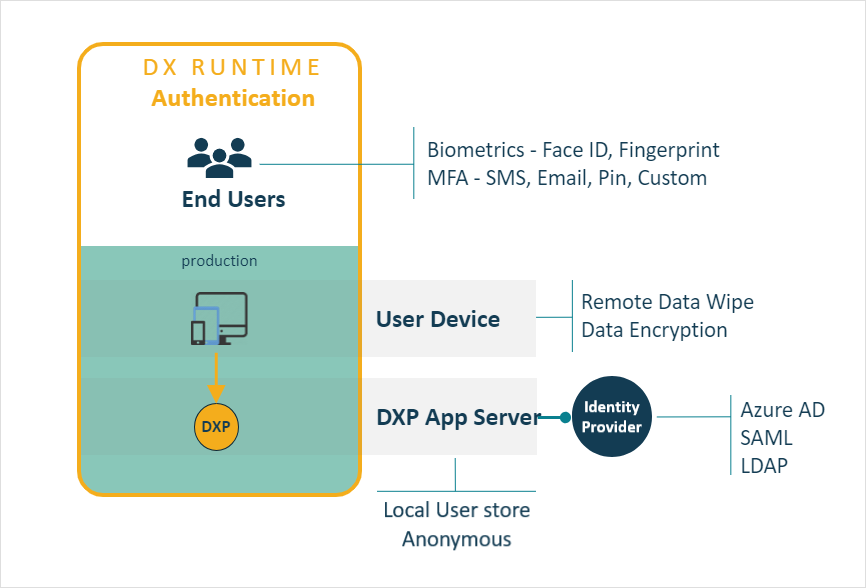
Runtime security
Carefully managing credentials and locally stored data is a key cornerstone of a security system. Neptune DXP applications accessed by end users offer support for:
-
User Authentication through multiple mechanisms
-
Role-Based Access Control for fined grained authorisation control
-
Self-Registration for business with substantial workforce sizes, to simplify the onboarding process
-
Data Protection encrypting local cache data
User authentication
Neptune DXP supports multiple authentication mechanisms through native integration with the following identity providers:
-
Microsoft Entra ID in this case the Neptune DXP application is integrated with the Microsoft identity platform by registering it with an Microsoft Entra ID tenant, providing secure sign-in and authorization.
-
SAML2 for federated identities authentication.
-
LDAP Integration whereby the whole directory is imported or in part by searching for a specific subset of users; support is provided on-premise Microsoft Active Directory or any other standard LDAP solution, e.g. on-premise Microsoft Active Directory or other LDAP solution.
-
Local User Store where use of an IDP is unavailable. Neptune DXP provides a comprehensive mechanism to implement a configurable password policy.
-
oAuth2.0 is a common authentication for 3rd party services.
-
OpenID will be supported from DXP22 version onwards.
-
Custom Authentication allowing the use of a bespoke script driven mechanism to be built.
-
Anonymous Login for public access, for example, kiosk, consumer web apps, with no login required:
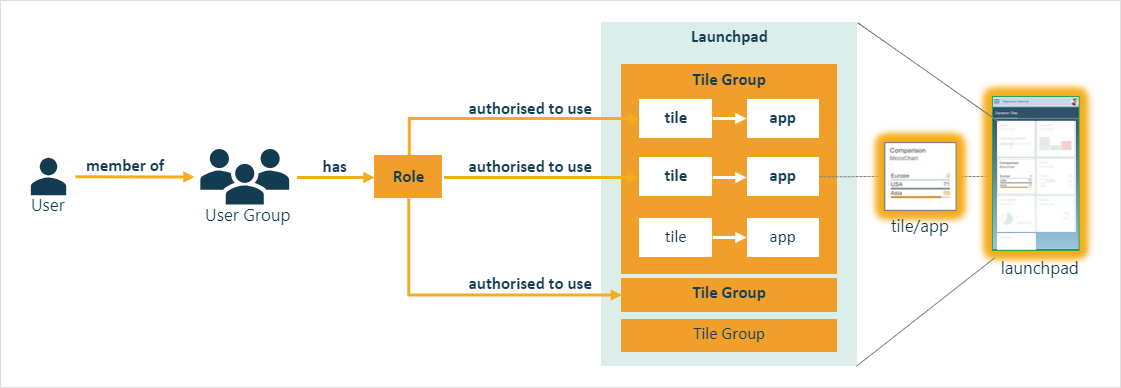
Role based access control (RBAC)
Once users are authenticated their user account is used as the basis to establish the level of access to Neptune DXP runtime apps and functions. To facilitate a fine level of access, but also to enable the segregation of duties, the Neptune DXP platform implements the following authorisation model:
Let’s consider a case study concerning a typical Finance Accounts Payable (AP) business unit to put the above, somewhat abstract, elements into a real-life context.
In our case, the AP team has been experiencing an increasing volume of request from multiple warehouse distribution centres (DC) to initiate small charges to transportation companies when they breach their agreed SLAs, for example, late truck arrival, incomplete orders or damaged goods. To deal with this problem the AP team has commissioned a solution to automate the process of invoicing transportation companies (treated as vendors) using the following Neptune DXP apps:
-
Charges application a simple purchasing/invoicing application to support the entry of vendor charges
-
Approval application authorising charges above a certain threshold
-
Contacts application capturing the vendor’s employees as contacts (for example,name, email, phone etc.)
-
Mailshots application compiling and sending templated emails for example, mailing a charge invoice or weekly report
The user community within the AP and DC functions are organised into general roles representative of their daily duties but not strongly coupled to their organisational positions:
-
AP Supervisor, oversees the activities of the AP specialists; initiates and manages payment runs
-
AP Specialist, edits invoices, ensuring accuracy, uniqueness and completeness; matches invoices to correct purchases orders or receipts ensuing that invoices comply with company policy
-
DC Supervisor: creates invoices for charges to be applied to transportation companies
These roles are then organised into groups to facilitate access to the apps:
-
AP Managers group
-
User Roles: AP Supervisor
-
Users: employees of the Finance AP team
-
-
AP Administrators group
-
User Roles: AP Specialist
-
Users: employees of the Finance AP team
-
-
DC Administrators group
-
User Roles: DC Supervisor
-
Users: employees in the various Distribution Centres
-
When a user is created and assigned to a group, they will inherit all the roles associated into that group. This eliminates the need for repeat roles assignment to individual users. In the context of a large enterprise a user group is likely to have multiple roles some function whilst many will be for cross-cutting concerns such as health & safety, security, HR attendance.
With the apps built, the following Launchpad facility is created to manage access to the vendor charges process:
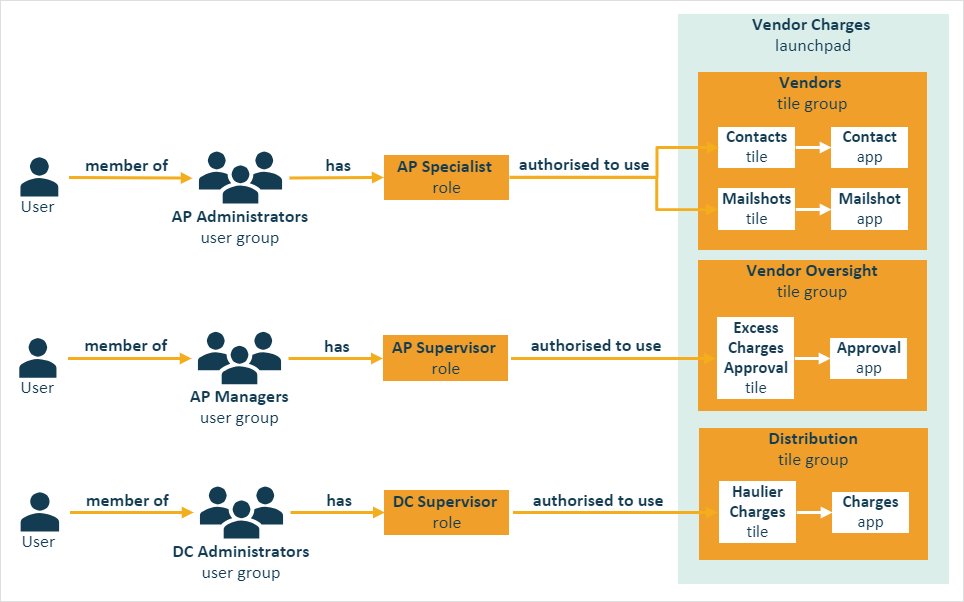
It composed of three tile groups that will host apps inside individual tiles:
Vendor Charges Launchpad composed of:
-
Singleton Launchpad Tiles: n/a
-
Vendors Tile Group, associated to:
-
Tiles: Contacts, Mailshots linked to the corresponding contact/mailshots apps
-
Roles: accessible only by AP Specialists
-
-
Vendor Oversight Tile Group
-
Tiles: Excess Charges Approval linked to the vendor approvals application
-
Roles: accessible only by AP Supervisors
-
-
Distribution Tile Group, associated to:
-
Tiles: Haulier Charges, linked to the vendor charges application
-
Roles: accessible only by DC Supervisors
-
The above model allows for DC Supervisor to enter charges against their haulier vendors. AP Specialist then verify them and pay them. If a charge is over a maximum threshold an AP supervisor can clear it or reject its payment and finally the AP specialist can onboard a vendor contact to email them a charge invoice along with a weekly statement.
Neptune DXP’s Role based authorisation model allows for the definition of fined grained access to apps whilst minimizing the work required at user level. Coupled with the integration to an Identify Provider such as Microsoft Entra ID means that a user and its associated group can be automatically claimed at the time of logging into the Neptune DXP app, including changes to their user group assignments. The bulk of the authorisation work is then limited in structuring the application Launchpad hosting the apps and the access rights to individual user roles.
Self registration
The Neptune DXP supports the self-registration users that have an email with a specific domain name. For example, if your company employees have corporate email addresses you can offer them the option to self-register to simplify and, potentially, reduce the cost of onboarding. Neptune DXP allows you to implement on or more apps targeted to a group of employees, partners or customers and deploy them into an application Launchpad specifically configured to support self-registration.
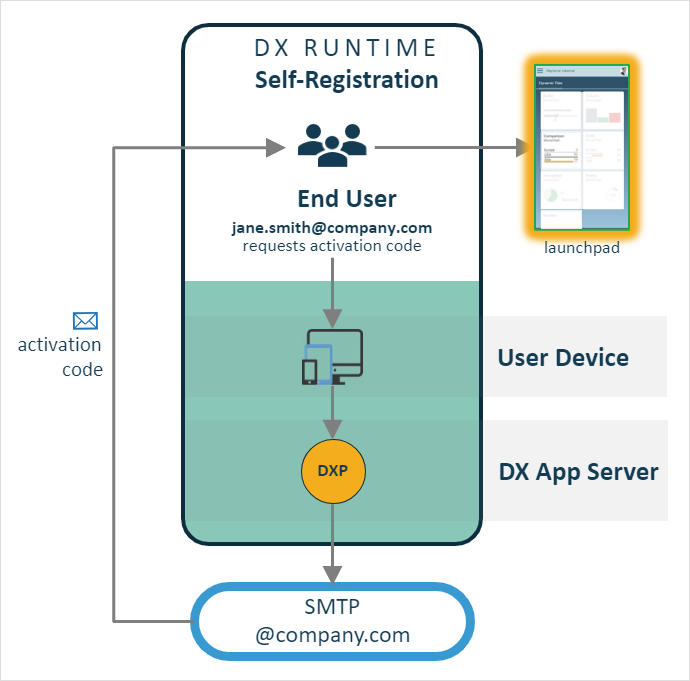
The following steps take place to complete a self-registration process:
-
The User:
-
logs in for the first time providing a valid corporate email address, for example,
jane.smith@company.com -
requests an activation code (offered as an option in the UI)
-
-
Neptune DXP will generate an:
-
activation code,
-
activation email based on a configurable email template
-
activation email via the corporate email service (SMTP), integrated with Neptune DXP
-
-
The User:
-
enters the activation code in the login screen
-
authenticates to use the app and gains access to the Launchpad
-
Access to the apps for self-registered users is subject to role based access controls.
Data protection
Data held in Neptune DXP apps can be, via a simple setting, be encrypted using the Advanced Encryption Standard (AES) utilising a 256-bit encryption key. When data is stored in the cache it is automatically encrypted and when fetched back to present to the user interface it is automatically decrypted:
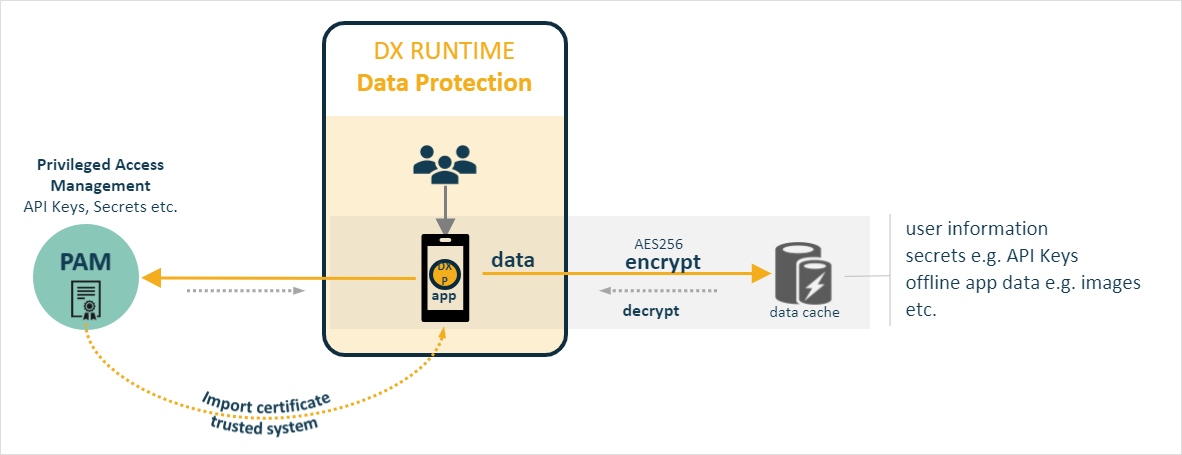
Whilst the strong encryption of app data should suffice for all use cases, you may already operate a privileged access management service, for example, Microsoft Azure or Hashicorp Vault, acting as a secure storage for enterprise secrets such as credentials, API keys, passwords, license keys.
In this case the Neptune DXP app can onboard the REST API of the PAM service and enable key based access to secrets to further mitigate security concerns. To establish a trusted relationship between the PAM service and Neptune DXP app the recommended approach is to use a certificate-based authentication mechanism. The PAM service must issue a certificate that s imported into Neptune DXP and to create a certificate-based API authentication policy. The policy is assigned to the on boarded PAM REST API ensuring that each API call made from Neptune DXP runtimes is authenticated and accepted. The use of certificates is recommended because credential driven methods (for example, basic authentication or token based) require a sensitive secret, that is, password or a token to be stored in the local device.